Quickie: What network ports are listening on my machine in PowerShell?
My customer is considering some firewall changes and wants to know what they'll break if they block a laundry list of inbound ports in the Windows Firewall. What will that break? I don't know. Let's inventory the machines and see what's currently listening.
Here's how to get the listening network ports in PowerShell.
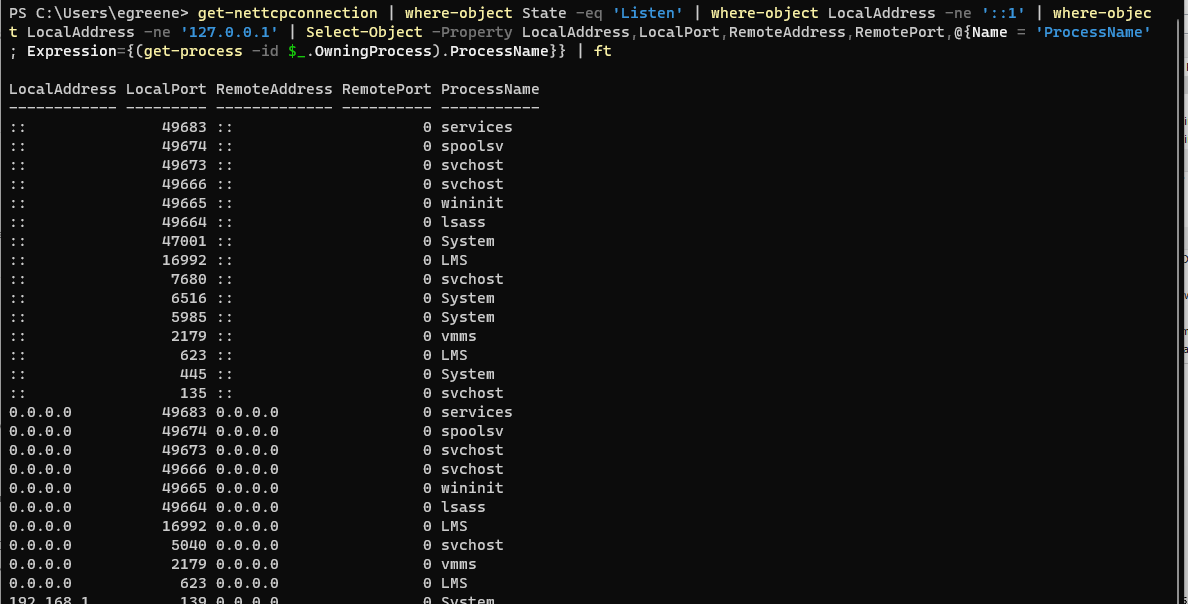
get-nettcpconnection | where-object State -eq 'Listen' | where-object LocalAddress -ne '::1' | where-object LocalAddress -ne '127.0.0.1' | Select-Object -Property LocalAddress,LocalPort,RemoteAddress,RemotePort,@{Name = 'ProcessName'; Expression={(get-process -id $_.OwningProcess).ProcessName}} | ft
Get-NetTcpConnection returns all of the listening and active TCP connections, similar to the old netstat command. The three where-object commands filter in only the Listening connections, and then filter out things listening on the IPv6 and IPv4 loopback addresses respectively. Then it's pipelined through select-object to resolve the numeric process IDs to human readable process names. Finally ft, short for format-table, drops it into a tidy output.
HTH


Comments